Publication Date
The ABC’s of cloud security

Cybersecurity encompasses a whole range of processes and tools used to protect your organization and its assets from attacks. In a cloud environment, the democratization of data access makes it more difficult to monitor how data is used, and most importantly, where it travels. The ability to access digital assets any time, anywhere, and on any device presents novel challenges and threats for companies.
Simply put, you need to make sure data doesn’t end up on less secure storage solutions outside your security perimeter while preventing people without authorization from accessing it. You also need to neutralize intentional and unintentional threats from within the organization. No mean feat!
As you may have guessed, there is more than one way to get the job done when it comes to cloud security, and there are still a lot of grey areas. Responsibility for security is shared between a company’s service providers and their IT teams. Understanding the basic roles and responsibilities is a big part of preventing security breaches that could be exploited by unscrupulous individuals.
The nuts and bolts
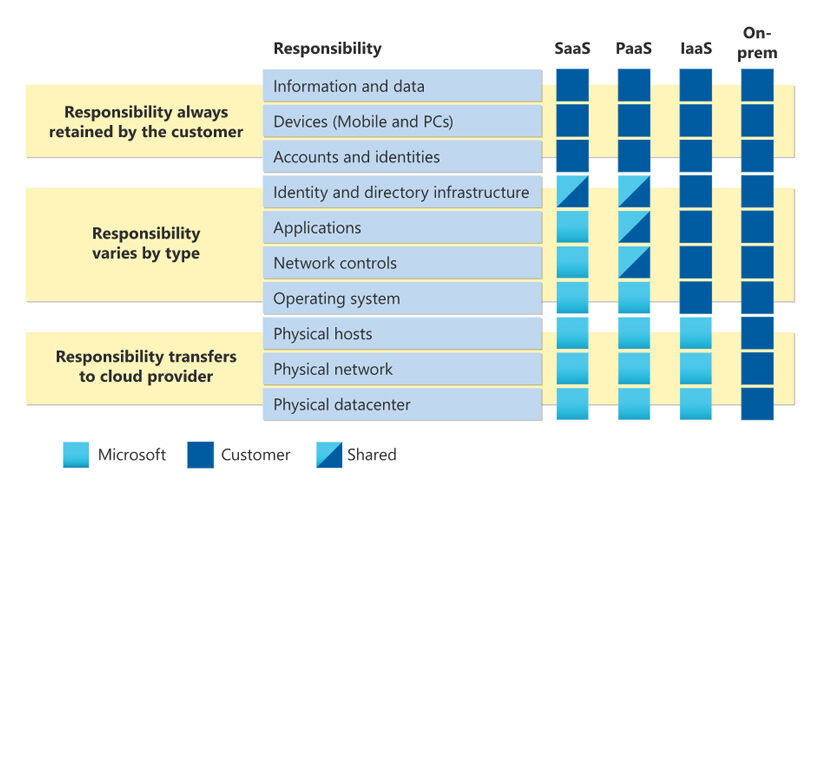
There are four types of cloud computing.
Every organization has to choose an option based on their business needs and objectives. The type of service provided by the environment is a factor and a variable they’ll need to adapt to and has direct impact on the division of security-related responsibilities.
Flexible responsibilities within a clearly defined scope
Infrastructure as a service
In an infrastructure as a service (IaaS) model, your provider must secure the basic cloud infrastructure, which includes everything underneath the operating system. You are responsible for applications, data, runtimes, access, users, and their devices.
Platform as a service
If you use the platform as a service (PaaS) model, your service provider will have broader responsibilities. In addition to the infrastructure, they will also need to protect the operating system, middleware, and runtimes. You are in charge of security for applications, data, access, users, and their devices.
Software as a service
Many companies opt for software as a service (SaaS), like Microsoft 365. With SaaS, you have less control, but you still have to make sure the data and the users and their devices are secure.
Regardless of how the responsibility is divvied up, you will always need to make sure the procedures and strategies are in sync with the four pillars of security: limit access, protect data, respond, and recover.
Target: Zero Trust
When it comes to information security, we tend to assume that a company’s firewall is enough to keep the workplace safe and secure. Working in a cloud environment built on that premise—where most of your infrastructure, and especially your users, are located outside the network perimeter—exposes you to a number of threats.
The Zero Trust model is based on the principle that access and data breaches can happen at any time and that every request must be verified, regardless of its source.
Information is gathered and analyzed in real time to automatically detect and instantly address anomalies. Read this article to learn more about Zero Trust.
Implementation and best practices
Something like the Zero Trust approach should be the cornerstone of your cloud security processes and strategies and be applied in alignment with your governance and compliance rules. The recommended roadmap includes:
These security tools do more than address weaknesses from both internal and external threats. As you know, they also help correct any errors that may occur during development or configuration modification. Plus, they minimize the risk that people without authorization will access sensitive data.
Companies rely on cloud computing to stay at the head of the pack. And now you know that the risks can be mitigated by strictly applying practices that will help your organization meet these security targets. Choosing seasoned professionals who know the ins and outs of this wide-ranging field will help you stay on top of industry best practices and eliminate blind spots.
