
Sales organizations
A sales representative plans to hand in his resignation next week and is moving to a competitor. What’s stopping him/her from downloading the customer database?
When it comes to data security, it’s dangerous to assume your organization is fully protected. Often, the greatest cyber security risks are internal, stemming from the everyday use of your Microsoft Office 365 apps.
Outlook, SharePoint, OneNote, Teams, these everyday communication and collaboration tools may be the biggest cyber security threat to your organization because of what you think is protected. Even if you set up the best security and monitoring devices for your corporate data, without understanding the context of who is accessing your data, and how and where they are using it, you cannot fully protect yourself. This aspect is central to compliance with Quebec’s Law 25.
With Microsoft Office 365 you are ensured Microsoft manages and guarantees security of their cloud infrastructure as well as data and service availability. Your organization still has a lot of responsibilities on your end, as depicted in the graphic below.
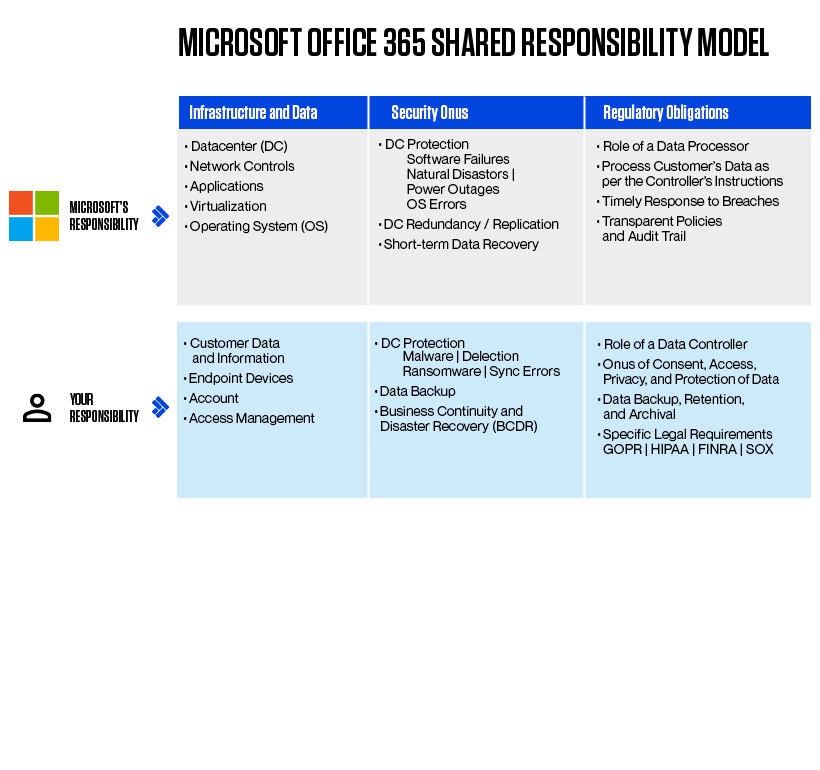
These are some examples of the potential risk you’re taking without strict data governance across your on-premises, cloud, and hybrid sources.
With Sergio Londono
Microsoft Purview specialist at ITI

Ensure sensitive information uploaded in a shared folder can only be viewed, shared,
printed or edited with authorized access rights.

Protect content in external emails so it cannot be opened, copied, shared or edited
unless individual recipient has authority.

With Sergio Londono
Microsoft Purview specialist at ITI

Configure accessibility for authorized users to work from unknown devices based
on strict rules using container classifications.

With Sergio Londono
Microsoft Purview specialist at ITI

Set rules and parameters to ensure the internal and external sharing of specific files
and sensitive data is protected.

To be fully in compliance with strict data privacy and protection regulations like Quebec’s Law 25, now’s the time to make sure your security parameters are up to par. See how to automatically set customized and configurable security measures for all content shared via Outlook, Sharepoint, Teams, One Note and more.